Resources
Access a wealth of complimentary resources: videos, white papers, podcasts, and more, designed to strengthen your understanding of compliant data destruction, secure e-waste disposal, and efficient asset recovery solutions. Empower your decision-making and protect your business with professional guidance at your fingertips.


What is ITAD?
Understanding what IT asset disposition is and why ITAD is important starts with recognizing that end-of-life technology represents both risk and opportunity. ITAD — which stands for IT Asset Disposition or Disposal — encompasses the secure, compliant, and value-maximizing processes for retiring technology equipment. ITAD is a comprehensive process that securely retires end-of-life technology equipment while maximizing value recovery, ensuring data security, and maintaining environmental compliance. This includes everything from secure data destruction and equipment remarketing to certified e-waste recycling, all conducted through auditable processes that protect your organization from risk. As a leading ITAD specialist for over 25 years, we handle the entire lifecycle from equipment pickup through final disposition with full chain-of-custody documentation.
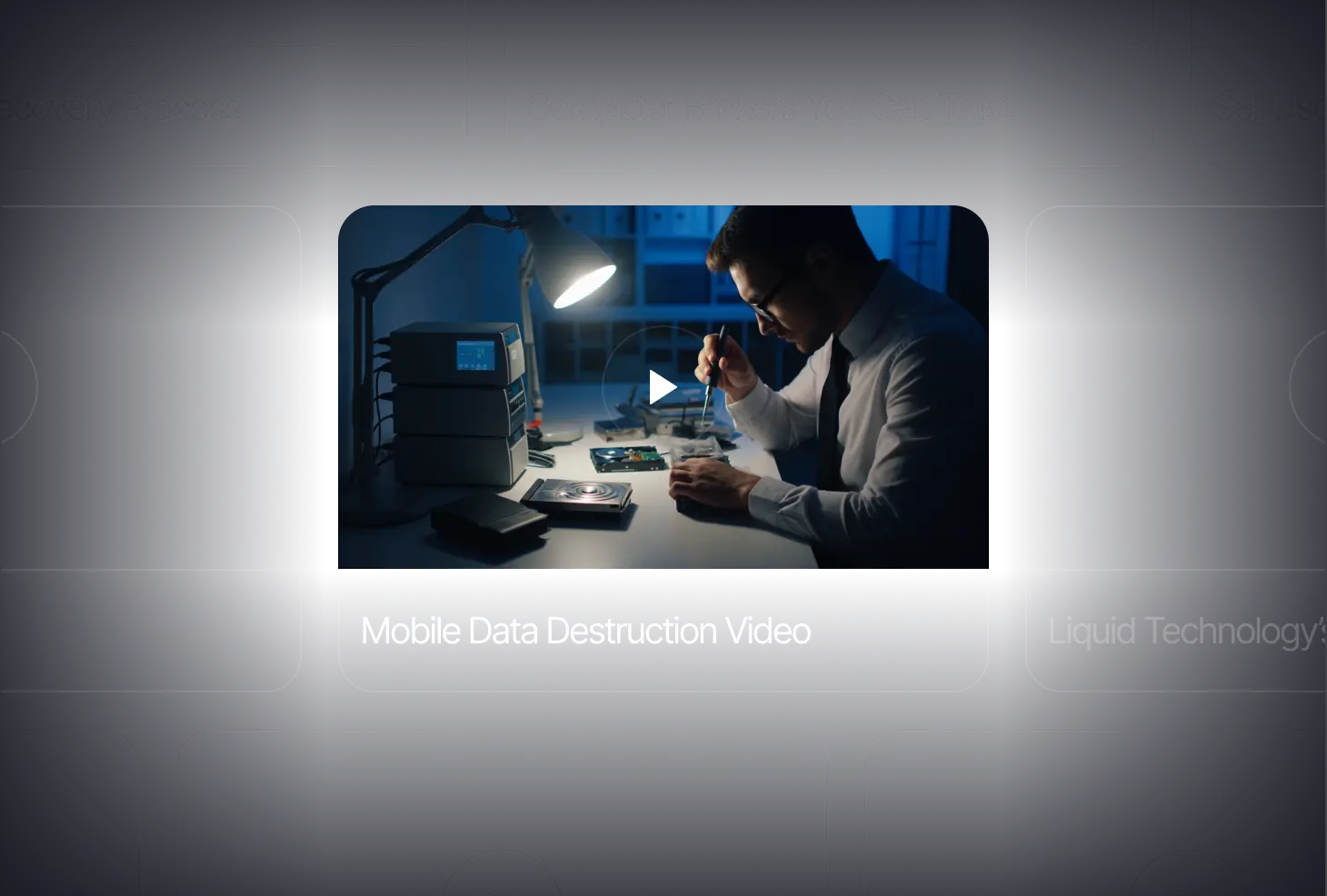
Videos
When you choose Liquid Technology for secure asset management services, data destruction, or e-waste recycling, you can trust that your company's sensitive information is fully protected. Our video library provides a firsthand look at our state-of-the-art facilities and certified processes in action.
Watch the Videos
White Papers
Before you choose a company for your computer liquidation services, you should have an understanding of what it takes to provide secure and compliant data destruction. In our free downloadable white papers, we break down the process and explain what to look for when evaluating ITAD partners.
Download Our White Papers
Case Studies
Read firsthand accounts of how we've helped businesses successfully reach their operational goals through exceptional ITAD service. Visit our case studies page to discover how we've resolved complex IT asset disposition challenges across industries, from data center decommissioning to global equipment liquidation projects.
Read Our Case Studies
Podcast
Our podcast features IT and tech professionals sharing insider insights on data destruction, cloud migration, ITAD best practices, and other critical topics. Explore these expert industry conversations and gain valuable perspectives from leaders in technology asset management and secure disposition.
Listen to Our PodcastFAQs
Frequently Asked Questions about IT Asset Disposition & Recycling
Looking for an e-Waste Recycler?
As one of the industry’s leading IT asset disposition service providers, Liquid Technology provides a suite of effective impartial solutions. Discover what to look for in a quality e-waste recycler.
Download GuideContact
Please complete the details below and we’ll connect you with an expert.
